How secure are your IoT devices? With the proliferation of smart technology, ensuring the security of these devices has become paramount. A bold statement to consider is that without proper firewall configurations, even the most advanced IoT devices can become vulnerable entry points for cybercriminals. Understanding how to manage and configure firewalls effectively is no longer optional but essential for both individual users and large-scale enterprises.
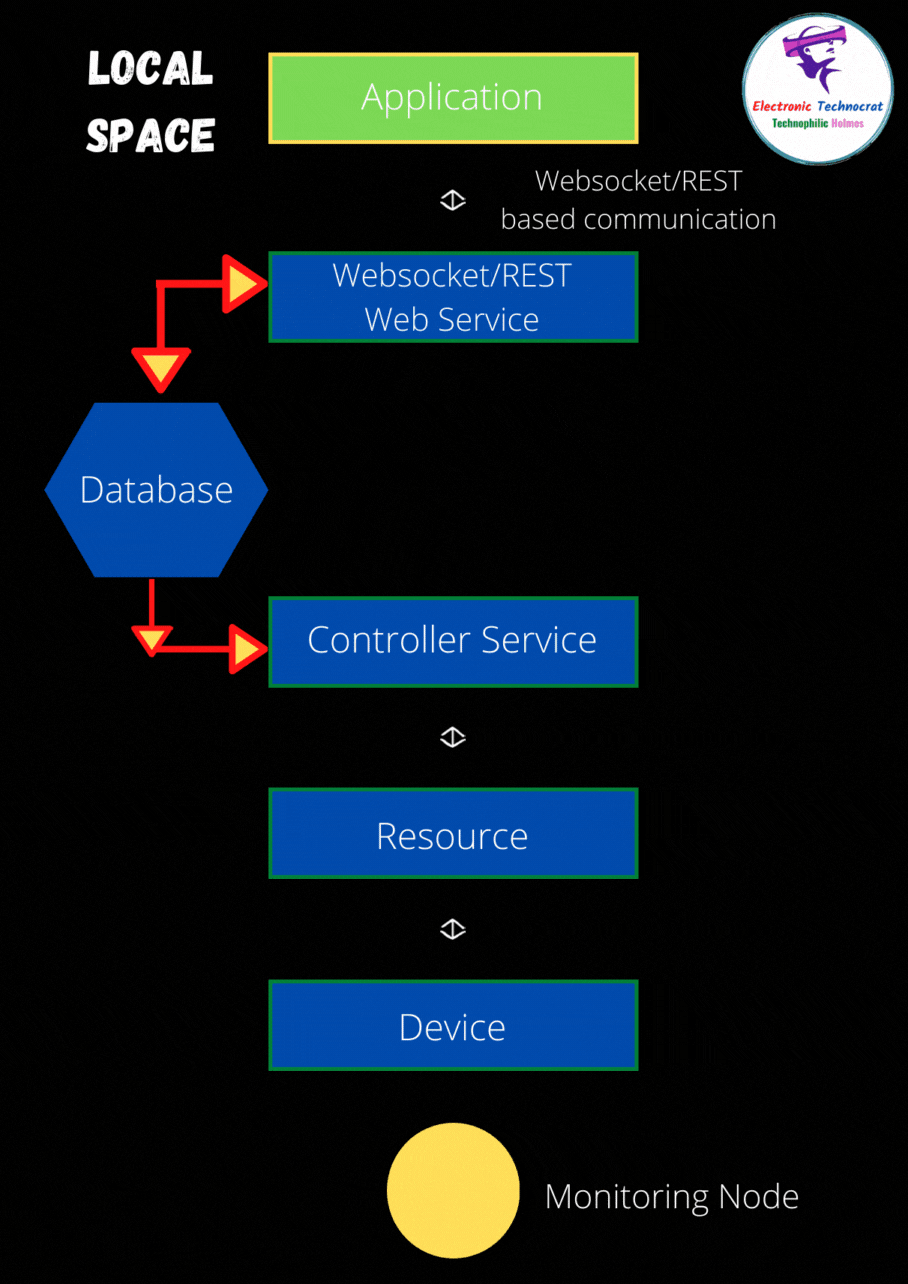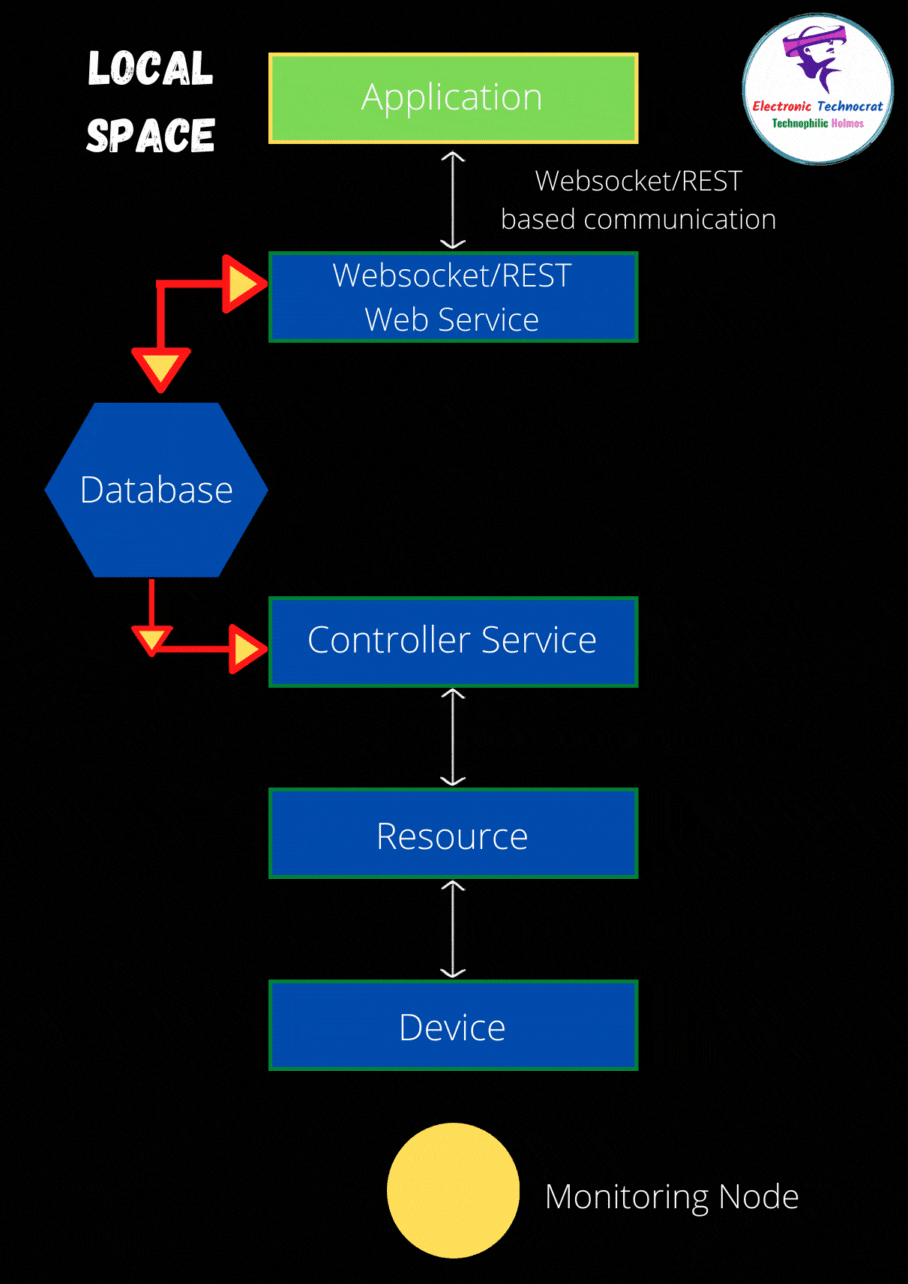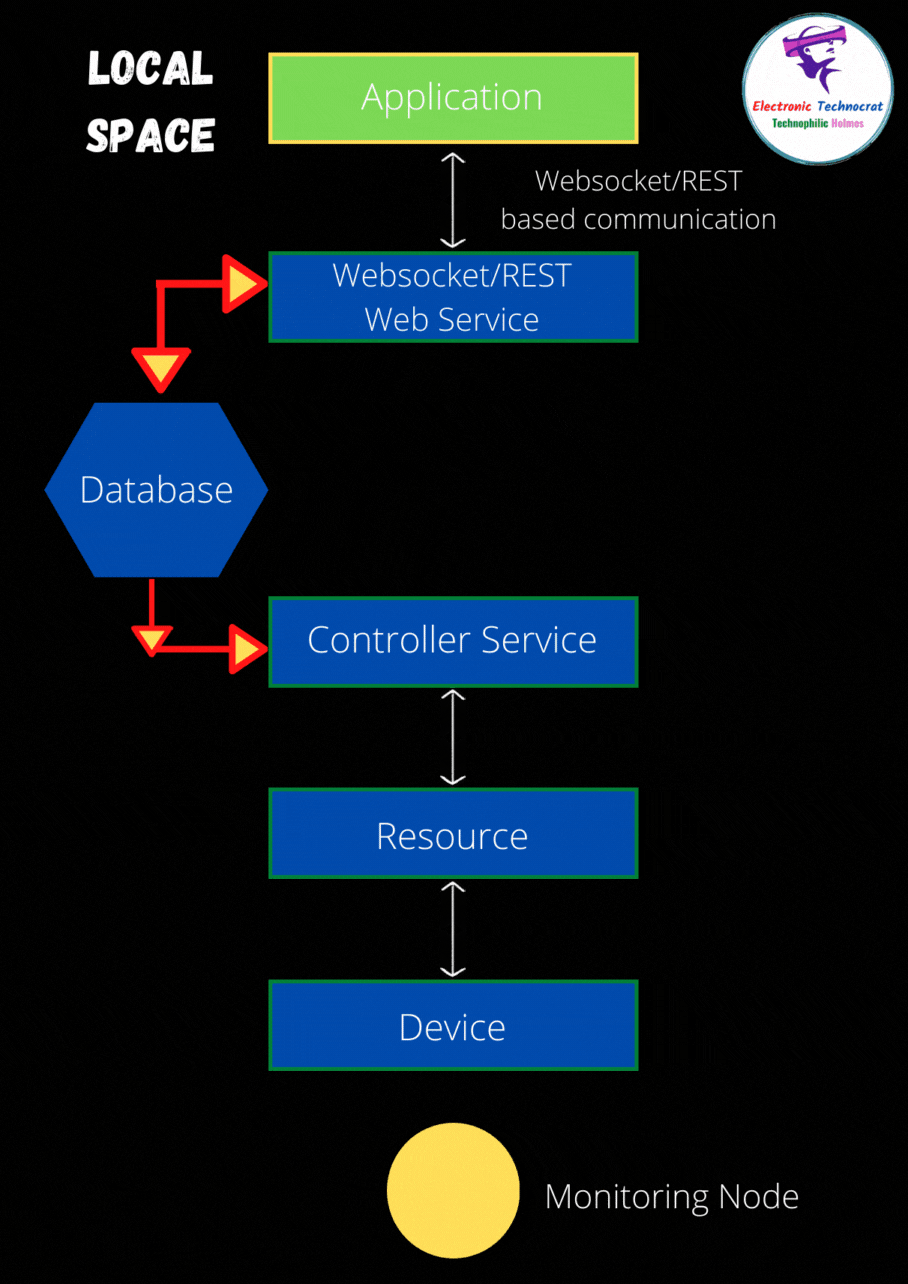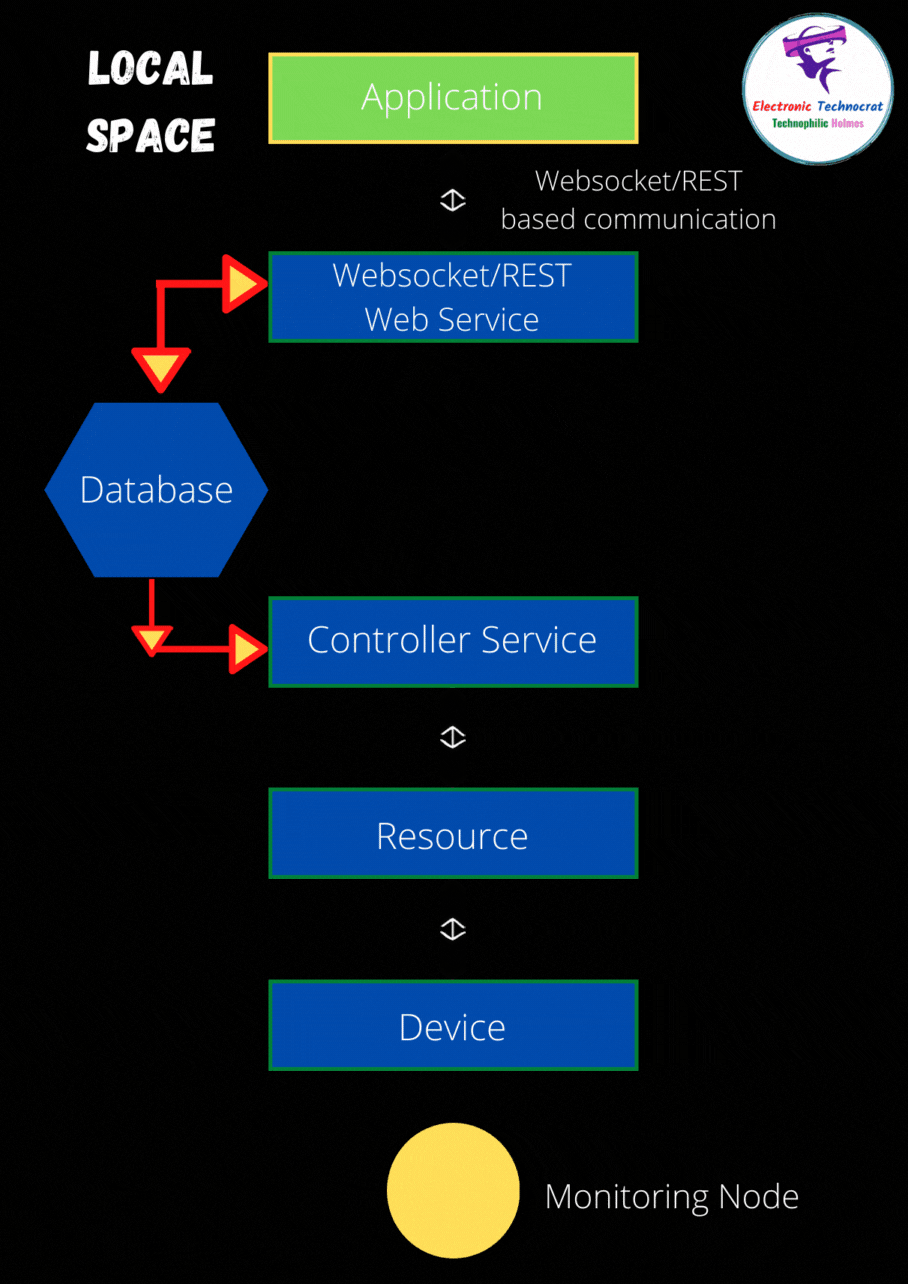
In today's interconnected world, securing IoT devices involves more than just setting up basic passwords or enabling encryption protocols. For instance, imagine a scenario where a Greengrass core device is situated behind a restrictive firewall that blocks all incoming connections. This setup poses challenges in managing and accessing such devices remotely. To address this issue, solutions like AWS IoT Greengrass offer secure tunneling capabilities, allowing administrators to access devices securely without modifying complex firewall settings.
| Category | Details |
|---|---|
| Name | AWS IoT Device Management |
| Region | US East (Ohio) |
| Professional Information | Centralized management system for IoT devices deployed across various environments |
| Career Focus | Enabling remote access to IoT devices located behind firewalls |
| Reference Website | AWS IoT Greengrass Documentation |
Firewall management plays a crucial role in enhancing smart home security. By meticulously monitoring and controlling network traffic based on predefined rules, firewalls act as the first line of defense against unauthorized access. However, setting up effective firewall rules requires a comprehensive understanding of both the network architecture and potential threats. For example, an Azure IoT Edge device operating behind a firewall necessitates specific rule configurations to ensure uninterrupted communication with its public REST API while maintaining robust security measures.
Remote access to IoT devices often presents unique challenges, especially when these devices are situated behind NAT routers or firewalls. Platforms such as SocketXP provide innovative solutions by enabling secure SSH access over the internet using SSL/TLS VPN tunnels. This approach not only simplifies remote management but also ensures data integrity and confidentiality during transmission. Moreover, integrating advanced tools like UniFi Dream Machine into home networks allows users to implement VLAN segmentation, thereby isolating IoT devices from other network components and reducing potential attack vectors.
Palo Alto Networks' Panorama offers centralized firewall management capabilities, streamlining operations across multiple locations. Through a unified security rule base, Panorama facilitates consistent threat prevention, URL filtering, application awareness, and user identification throughout the entire network infrastructure. Such centralized control significantly reduces complexity and saves valuable time for IT teams tasked with overseeing extensive network environments.
AWS IoT Device Management pricing reflects the value provided by its comprehensive suite of features designed to support diverse deployment scenarios. Whether managing a single device located behind a restricted firewall or orchestrating thousands of devices distributed globally, AWS IoT Device Management adapts seamlessly to meet varying requirements. Its ability to function efficiently within confined network parameters makes it an ideal choice for organizations seeking reliable and scalable IoT solutions.
In conclusion, securing IoT devices demands a multi-faceted approach encompassing robust firewall configurations, efficient remote access mechanisms, and centralized management systems. As technology continues to evolve, staying informed about emerging trends and adopting best practices remains critical in safeguarding our increasingly connected world.
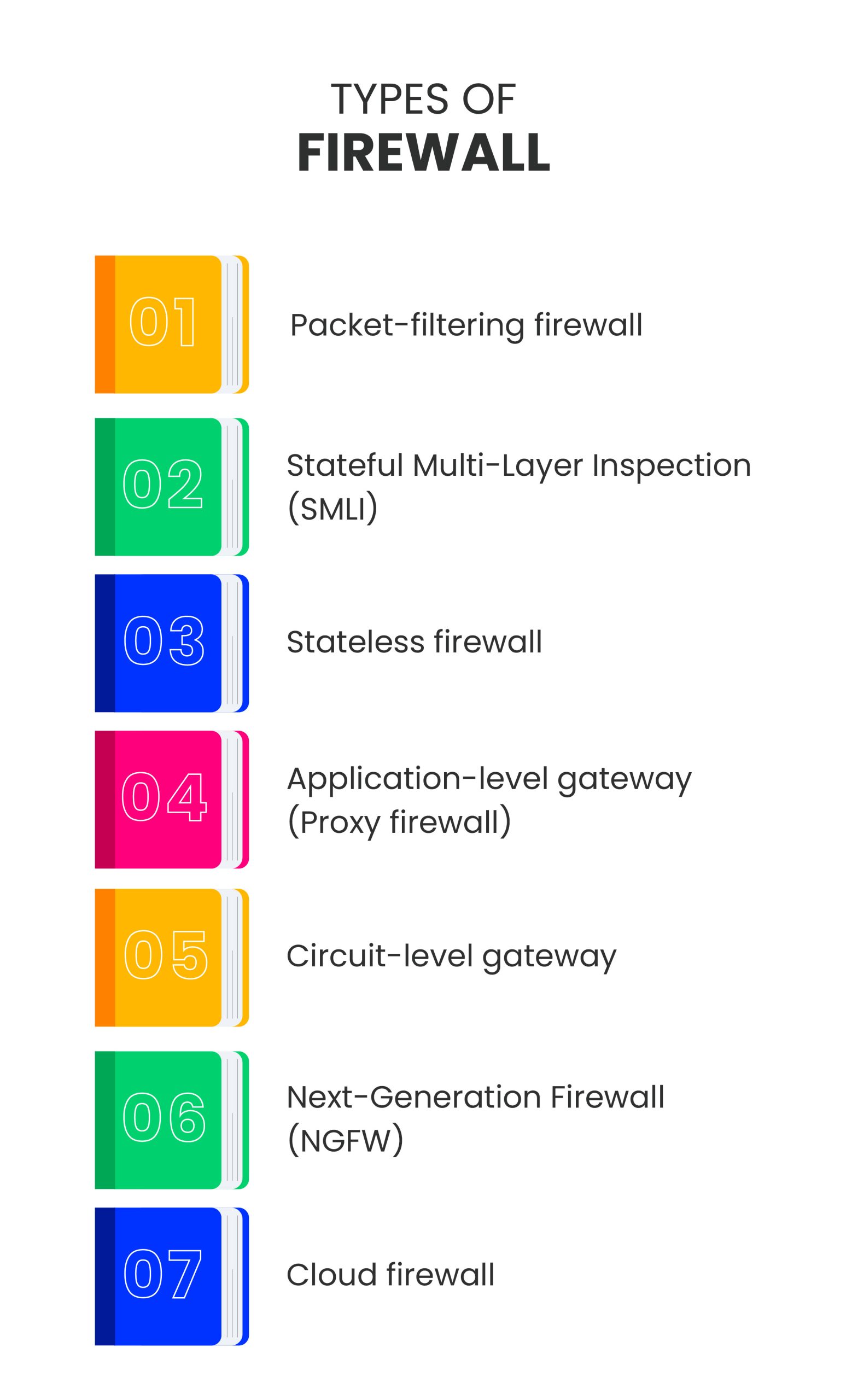
Additional considerations include evaluating different types of firewalls tailored specifically for IoT applications, understanding their distinct functionalities, and implementing appropriate strategies to mitigate risks associated with each type. Furthermore, educating end-users about potential vulnerabilities and encouraging them to adopt proactive security measures will contribute significantly towards building resilient and secure IoT ecosystems.
Ultimately, achieving optimal security for IoT devices requires collaboration between manufacturers, service providers, and end-users. By fostering awareness, promoting innovation, and adhering to industry standards, we can collectively enhance the overall safety and reliability of our digital landscapes. Remember, the strength of any network lies in its weakest link; therefore, prioritizing comprehensive security measures at every level becomes imperative.